
We're on day who-the-heck-knows of the Android Stagefright security vulnerability, and there's really no point keeping track of the days because no one's going to fix it. The Android ecosystem can't deal with security, and it won't change until it's too late.
Android was originally designed, above all else, to be widely adopted. Google was starting from scratch with zero percent market share, so it was happy to give up control and give everyone a seat at the table in exchange for adoption. The sales pitch was simple: "Apple locked you all out of the iPhone and with Microsoft you're just a customer, but on Android, you'll all have a say in the end product." The open source nature of Android allowed anyone to adapt its code to their hardware, and OEMs and carriers could (theoretically) alter or fork it to their hearts' content.
Now, though, Android has around 75-80 percent of the worldwide smartphone market—making it not just the world's most popular mobile operating system but arguably the most popular operating system, period. As such, security has become a big issue. Android still uses a software update chain-of-command designed back when the Android ecosystem had zero devices to update, and it just doesn't work. There are just too many cooks in the kitchen: Google releases Android to OEMs, OEMs can change things and release code to carriers, carriers can change things and release code to consumers. It's been broken for years.
The Android ecosystem's reaction to the "Stagefright" vulnerability is an example of how terrible things are. An estimated 95 percent of Android devices have a have a remote arbitrary code execution just by receiving malicious video MMS. Android has other protections in place to stop this vulnerability from running amok on your smartphone, but it's still really scary. As you might expect, Google, Samsung, and LG have all pledged to "Take Security Seriously" and issue a fix as soon as possible.
Their "fix" is going to be to patch 2.6 percent of all active Android devices. Tops. That's the percentage of Android devices that are running Android 5.1 today, nearly five months after the OS was released.
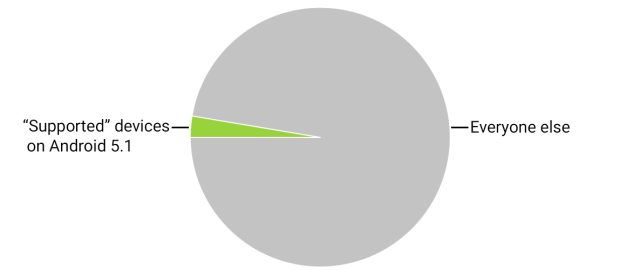
And 2.6 percent is a generous estimation for the top-end of "currently supported" Android devices in the wild. In reality, the number of devices getting a Stagefright patch will almost certainly be much lower.
Even assuming vendors put on the heat and do quickly fix all 2.6 percent of their Android 5.1-using supported install base, that still leaves 92.4 percent of Android devices worldwide vulnerable to Stagefright. (Remember, five percent of Android devices aren't vulnerable to Stagefright at all.) Android's layer-cake update strategy isn't even remotely appropriate for an OS that now has 24,000 individual active device models to address.
In a perfect world, the inability to update billions of potentially pwnable Android handsets would be enough to get Google, the OEMs, and the carriers to all sit down, set aside their branding guidelines and marketing department-enforced differences, and say, "We need to fix this." But we don't live in a perfect world. In the real world, carriers and OEMs want to keep their branding and customization hooks in Android so that they can advertise to customers with their own apps and interfaces. Neither appears to want to take responsibility for the unprofitable post-sale support of the millions of devices they create and sell.
At some point, a huge Blaster worm-style Android security armageddon seems inevitable—and that's what it's going to take to bring real, meaningful change. Stagefright is a big deal, and the Android ecosystem's reaction to it is literally 2.6/100ths of what it needs to be.
Look to Windows
Everyone likes to compare Android and iOS, but given that iOS hardware and software is owned and controlled by a single company, that's not really fair. For a much more appropriate model for what patching success looks like, look at Microsoft Windows.
Windows is Android's closest OS cousin in terms of varying hardware makeup, wide OEM support, and massive distribution. Microsoft has a centralized update system and an OS that ISPs and OEMs aren't allowed to touch; Comcast and Dell don't have a say in when your security updates arrive. Because hardware support is separate from the OS and no one is allowed to mess with the operating system, Microsoft has a single codebase for each Windows version to update, and this is the "mature" way to handle updates. It's a system with a distribution and speed that has managed to survive a continual security assault for years, and compared to the Android update situation, it's drastically different.A totally closed approach will never work for Android updates—Google can't put that genie back in the bottle—but to fix the current security nightmare, OEMs and carriers are going to have to accept a smaller level of access. Carriers should be limited, just as ISPs on a PC, to user-level applications. OEMs could also be limited to user-level apps and perhaps access to a comprehensive skinning system (like those that exist on many skins today), which should allow them to do the interface branding that they love without disturbing the underlying operating system.
Hardware support is also a sticky area. Android lacks the low-level hardware abstraction of x86 and Windows, where hardware drivers can live separately from the OS. ARM and Android still work with an embedded OS model, where there are no generic device drivers, making supporting every piece of hardware for every update a custom job. Fixing this is a really hard problem, as it would probably require support from Linux and ARM.
Android OEMs need to be soundly disabused of the idea that a two-year device upgrade cycle fits how long normal people own smartphones. Open Signal's just-released 2015 Android Fragmentation Survey says the most popular Samsung device in use today is the Galaxy S III, a three-year-old device. Of the top-ten in-use Samsung devices in the survey, six are older than two years old, and two are non-flagships that launched with an old OS and probably won't be updated.
The harsh reality is that OEMs and carriers only care about devices that are currently on sale—that's where the "two-year" plan came from. Samsung will rush to update the Galaxy S6, but going by Open Signal's numbers, the Galaxy S6 is only Samsung's 13th most-used phone. If the company really wants to protect its customers, it would update the Galaxy S III, S4, and cheaper devices like the Galaxy Grand Prime. The single top-ten device that Samsung shipped a Stagefright fix for is the Galaxy S5, which—shocker—is still for sale.
Microsoft, on the other hand, still provides security fixes for Windows Vista and everything after—meaning Microsoft has about 86 percent of its users covered. The remaining 14 percent are on Windows XP, where, after extending free support for two extra years because of XP's popularity, Microsoft still offers paid security updates for the 13-year-old OS. Eight years is probably a little excessive a time frame for smartphones—after all, eight years ago Android hadn't even been publicly announced—but it's not unreasonable to expect an OS ecosystem to aim for around 85 percent security update coverage.
The Android Ecosystem's lax attitude about security affects other parts of theses companies' business, too. Both Google and Samsung are trying to push into the enterprise market—Google has Android for Work, while Samsung has Knox—but Android's plummeting security reputation is going to hurt both of these platforms. Enterprises will have a hard time taking the devices seriously when Android is constantly in the news for security problems but iOS isn't.
Bumpy times ahead
With no real solution in sight, companies are simply applying Band-Aids to every scrape they can find. Android's application sandbox will hopefully limit any damage that exploits can do; the Play Store's walled garden will limit most users' exposure to malicious apps; and carriers are working to detect and block those malicious Stagefright MMS messages. The different stakeholders are doing everything except solving the root problem, which is simply that there's no way to actually deliver updates to the core OS for all affected users.
Google will almost certainly keep doing what it's been doing: moving more and more components into Google Play Services, but some bits will always require an over-the-air update. We already know what's going to be in the core of Android M, so it's clear that no comprehensive solution is coming soon.
There's too much disregard for the customer in the Android ecosystem to expect any of this get fixed proactively. Carriers and OEMs don't want to be relegated to the user space, and right now there are no repercussions for their self-centered actions. But consequences are coming. When the big Android malwarepocalypse does arrive, users won't care about the "two-year flagship" limit on patches if their phones stop working or their data gets stolen.
The Android update machine is broken, and in order to rebuild it in a way that works, we need to burn it down. Anyone have a match?
Update: In general, Google patches the AOSP code base for older versions of Android—currently Android 4.4 and up get security patches in a code base somewhere. The problem is that carriers and OEMs usually do not take this code base and turn it into an update for end users. Major OEMs have announced plans to do things a little differently for Stagefright specifically. Assuming carriers cooperate (In the US, so far only Sprint has indicated it will) it sounds like updates will hit flagships that are three years old and up (including the Galaxy S III and 4), which means our "2.6 percent" estimate could work out to be a little higher. Maybe Stagefright-specific fixes will come to 4 or 5 or 10 percent of the market.
In a statement to Ars a Google representative sent over the following bullet points:
- Currently 90% of Android devices have a technology called ASLR enabled, which helps protect users from this issue.
- We have pushed the fix and further safeguards to Nexus devices starting yesterday. We’ve already sent the fix to our partners to protect users. And, we'll be releasing it in open source.
- The next release of Messenger also contains a fix that helps mitigate the issue at the application level by requiring the user to click on videos before playing them, and will be rolling out this week. We recommend that Jellybean and above users switch their default SMS app for additional protection.
- Also, the most popular Android devices are getting the fix in August including
- Samsung Galaxy S6 Galaxy S6 Edge, Galaxy S5, Galaxy S4, Galaxy S3,
Note 4, Note 4 Edge- HTC One M7, One M8, One M9
- LG Electronics G2, G3, G4
- Sony Xperia Z2, Xperia Z3, Xperia Z4, Xperia Z3 Compact
- Android One
The crux of this article still remains though, updating flagships isn't enough to make a big impact on the user base, and that there is no scalable update solution for Android.
reader comments
403