
In 2011 and 2012, the NSA and the communications intelligence agencies of its "Five Eyes" allies developed and tested a set of add-ons to their shared Internet surveillance capability that could identify and target communications between mobile devices and popular mobile app stores—including those of Google and Samsung. According to an NSA document published by the Canadian Broadcasting Corporation, the targeting capability could have been used to launch "man-in-the-middle" attacks on mobile app downloads, allowing the NSA and other agencies to install code on targeted devices and gather intelligence on their users.
The document—a 2012 National Security Agency presentation obtained from former NSA contractor Edward Snowden—details efforts by the NSA, Canada's Communications Security Establishment (CSE), and the other "Five Eyes" allies to identify the "fingerprints" of communications between mobile devices and app stores. The capabilities were developed during two collaborative workshops: one in November 2011 hosted by the Australian Signals Directorate, and the other hosted by Canada's CSE in February 2012. The February workshop was attended by analysts from all of the Five Eyes communications intelligence agencies, the NSA slides joked, as "everyone wanted to experience a Canadian winter!"
These fingerprints were turned into "mini-plugins" for XKeyscore, the NSA's worldwide distributed Internet surveillance system. XKeyscore can apply these plugin rules to search through streams of Internet traffic for matching data. It has been used as a targeting system for various types of network exploitation attacks—including the "Quantum" man-in-the-middle attacks that allow the agencies to hijack or modify traffic between a computer or device of interest and various Web services to decrypt it, insert malware into the stream, or present altered versions of the content.
Blowing someone else's horn
While the document published by CBC does not indicate that the capability had been used in operations, it recounts a test operation called "Op Irritant Horn" (apparently named for the vuvuzela that gained worldwide infamy during the 2010 World Cup in South Africa) that confirmed such attacks were possible. The goal of the exercise was to "identify aggregation points for the mobile networks in the countries of interest" using the methods developed during the two workshops.
According to the NSA presentation by the agency's Network Tradecraft Advancement Team, those techniques included 17 XKeyscore filters that were developed for identifying app store traffic in non-"Five Eyes" countries. There were fingerprints based on the Google and Samsung app store protocols (Google's app store server in France was identified as an "aggregation point" for some of the targeted countries), as well as other application servers frequently connected to by mobile devices in those countries—including Congo, Senegal, and Sudan. Those included app stores hosted by providers in Cuba, Russia, Switzerland, Morocco, the Netherlands, the Bahamas, and Senegal.
The operation found a number of servers that were ripe for man-in-the-middle attacks, launching "effects" attacks on mobile devices and collecting device, user identification, and other data from information both moving between the stores and the mobile device and on the client device itself. For example, data collected by the CSE during Op Irritant Horn included the International Mobile Subscriber Identity (IMSI) and phone model data for customers of telecom provider Warid Congo—identifying the ZTE S213 feature phone as the most popular handset in Congo.
In an unexpected development, GCHQ analysts discovered a backdoor in the Chinese UCWeb mobile browser that was actively being used by another entity (whose identity has been redacted from the document) to conduct espionage. The backdoor "leaks" data, including the mobile device's IMSI and International Mobile station Equipment Identity (IMEI), unique GSM subscription identifier (MSISDN), and information about the device—including the user's e-mail address—all being sent back to a remote server. Some of the data exposed by this backdoor was associated with accounts on the Indian pay-as-you-go provider MobiMasti.
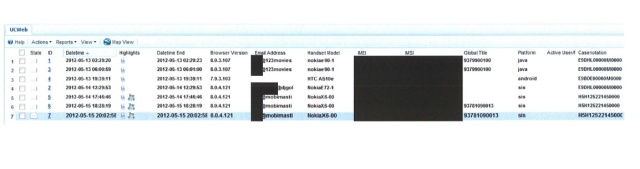
Spotting this exploit already in use created an opportunity for the NSA and the other agencies to build an XKeyscore filter to watch for the data being leaked by the backdoor so that they could passively capture it for their own purposes. It's yet another example of how the NSA uses passive surveillance to ride the coattails of other states' active network exploits for intelligence collection.
So you're exploiting a mobile app server...
In addition to building the 17 XKeyscore filters, another major task of the two workshops was to create a guide to reproduce the work for other mobile application services. The "tradecraft" used to identify and target app store servers was documented by the workshop group for analysts across all five communications intelligence agencies on event Wiki pages shared by the hosting agencies and on "Crafty Shack," a best-practices site shared across the five countries' intelligence communities.
The ten-step analytic procedure, "Identify servers communicating with a mobile network," is a recipe for targeting any Internet service used by mobile devices from a given mobile network, and it could be applied to any traffic dump. Much of the analysis done to profile mobile application servers by the NSA's Network Tradecraft Advancement Team was performed in Splunk, the commercial data analysis tool, as illustrated in the team's slide deck.
-
A simple flow diagram showing how the NSA's traffic analysis process identifies mobile app servers tied to a specific mobile provider of interest.
-
A slide showing profiling of mobile app servers from network capture data from the NSA's Network Tradecraft Advancement Team, with a Splunk screenshot.
These services might not include servers in "Five Eyes" countries, but they could certainly target the overseas servers of US companies—as demonstrated by the filtering of traffic headed for Google's French app store from African countries. When used in conjunction with the Quantum attack chain, the capability could be used to target not just app downloads but communication with any mobile service that doesn't rely on "pinned" certificates to communicate. The intelligence agencies could inject their own spoofed certificate to the client device and route all communications with a service through a fake server by way of BGP routing exploits.
Perhaps the biggest takeaway from the leaked document is that the NSA and other intelligence agencies discovered that third-party app stores—many of them poorly secured and some of them for jailbroken devices—are the primary source of apps for many countries. If you get malware on your device after downloading an app from one of those stores, it might not be the app developer's fault.
reader comments
57